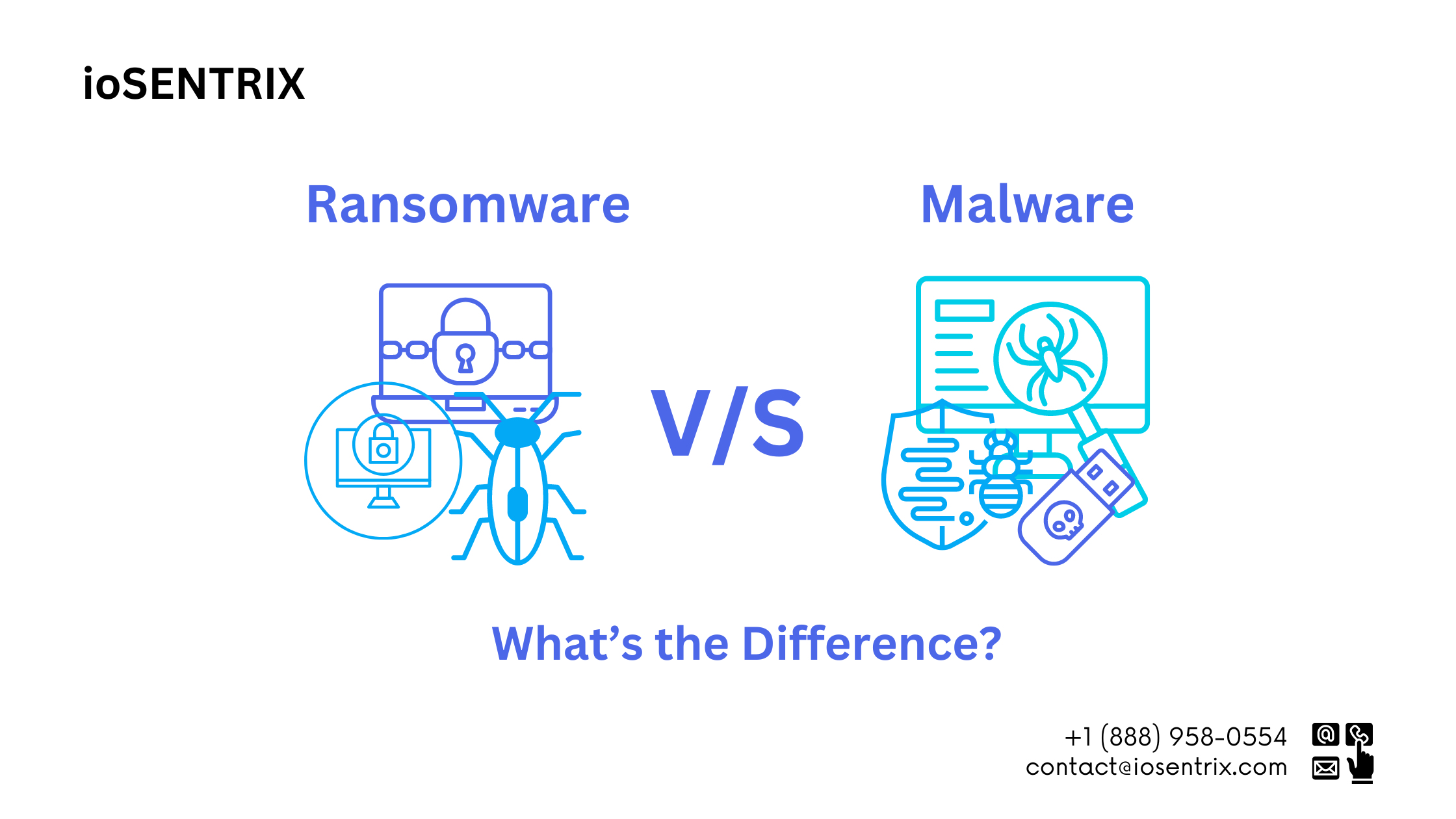
Explore →
Cybersecurity (62)
Covid-19 (4)
Telecommute (2)
Phishing (3)
RDP (1)
Bruteforce (1)
Windows (1)
Git (1)
SourceCodeDiscloure (2)
Vulnerability (42)
Pentest (6)
Pentesting (8)
BugBounty (2)
Risk-Assessment (5)
Third-Party (2)
Vulnerability-Assesssment (1)
VA (2)
Compromise-Assessment (1)
iot-security (1)
AppSec (2)
ApplicationSecurity (2)
SecureSDLC (4)
DevSecOps (35)
Vulnerability-Assessment (1)
Compromise Assessment (1)
Cloud Security (1)
OSINT (3)
osintincyber (3)
opensourceintelligence (3)
cloudsecurity (1)
cloudprotection (1)
log4j (1)
remotecodeexecution (3)
java (1)
vulnerability (1)
third-party (3)
XDR (1)
EDR (1)
Threat Detection (1)
SSDLC (1)
Security Requirements (1)
Application Security (37)
appsec (1)
applicationsecurity (1)
securesdlc (1)
devsecops (1)
phishing (1)
phishing-attacks (1)
cloud-misconfiguration (1)
compromised-credentials (1)
purple-teaming (2)
red-teaming (1)
offensive-security (1)
defensive-security (1)
testing (1)
penetesting (1)
Secure Medical Devices (1)
Appsec (1)
FDA-and-Cybersecurity (1)
Penetration Testing (32)
Secure SDLC (31)
 Never miss a story from us, subscribe to our newsletter
Never miss a story from us, subscribe to our newsletter